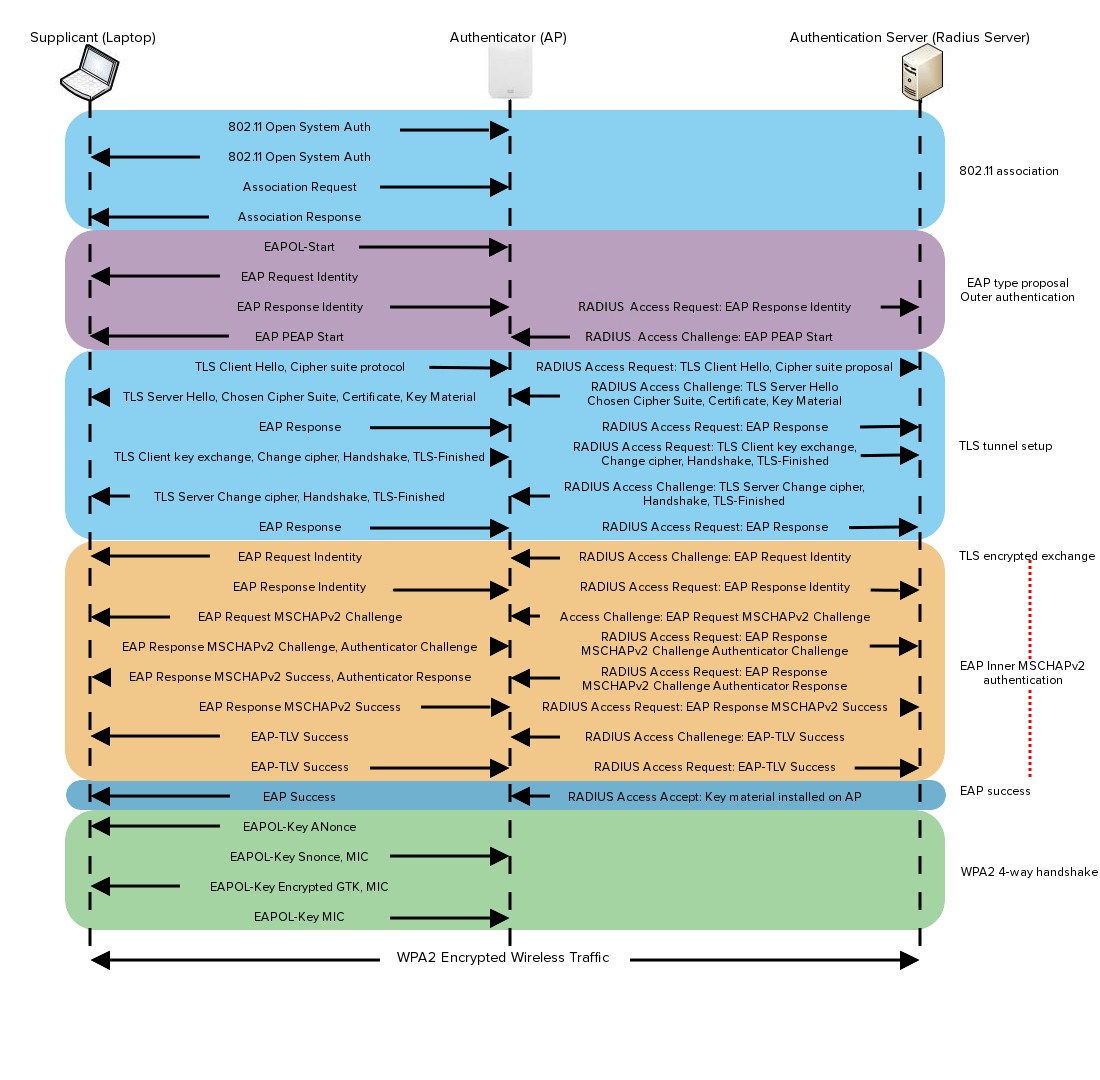
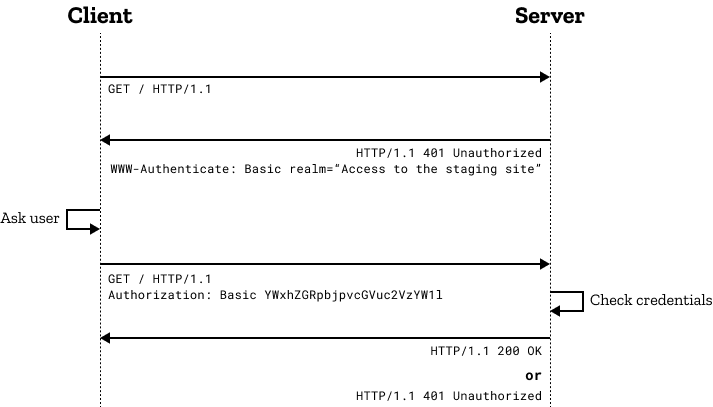
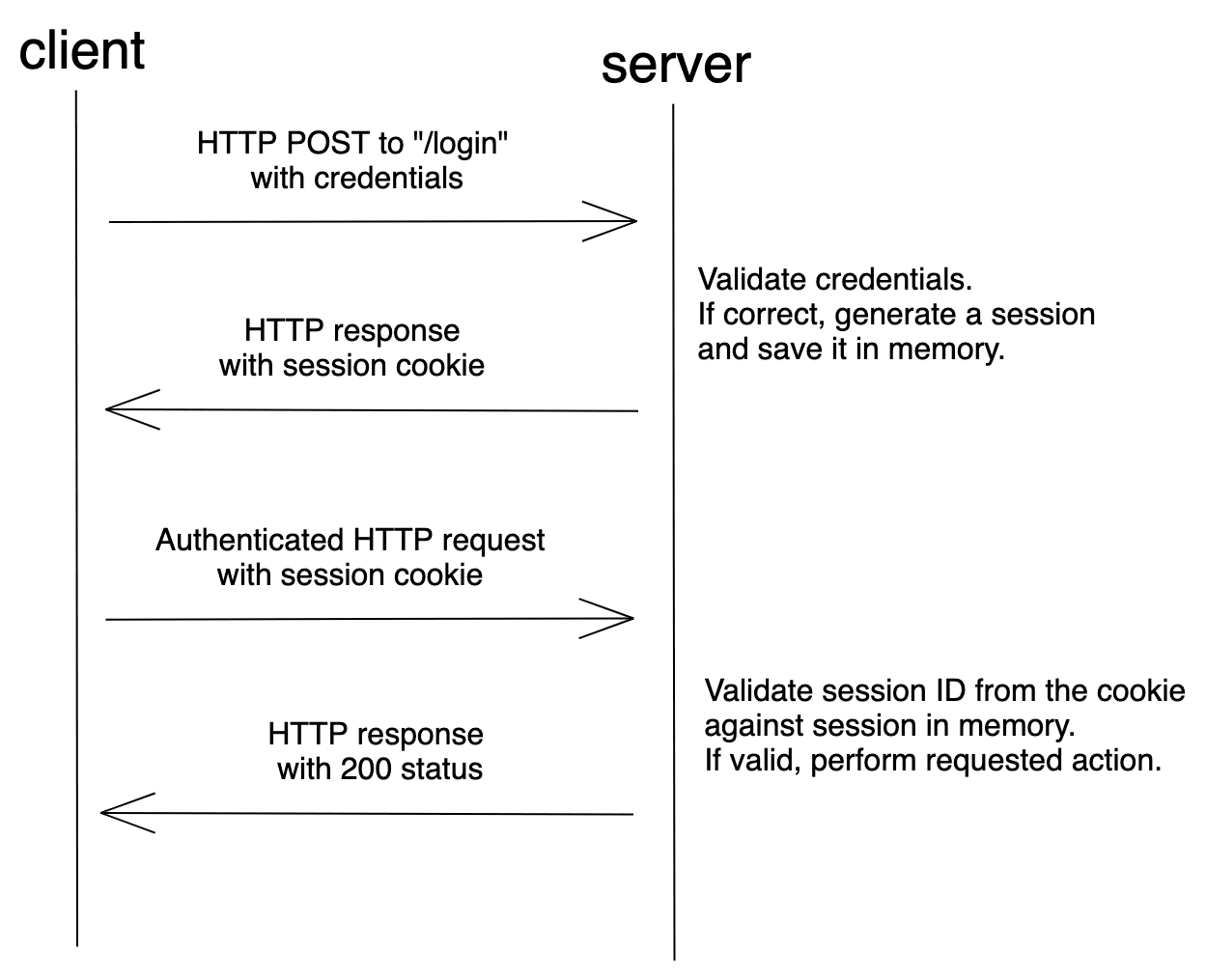
How Do You Authenticate, Mate?. A definitive guide to authentication… | by Ahmed shamim hassan | Better Programming
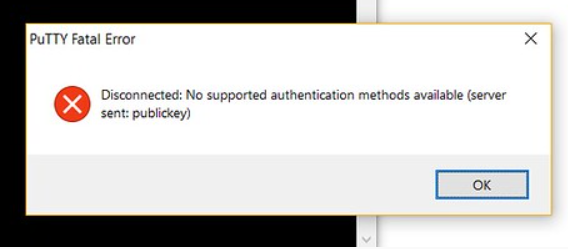
Error: "None of the authentication method supported by this client are supported by your server". | Web Hosting Forum - Review - Community & Resources

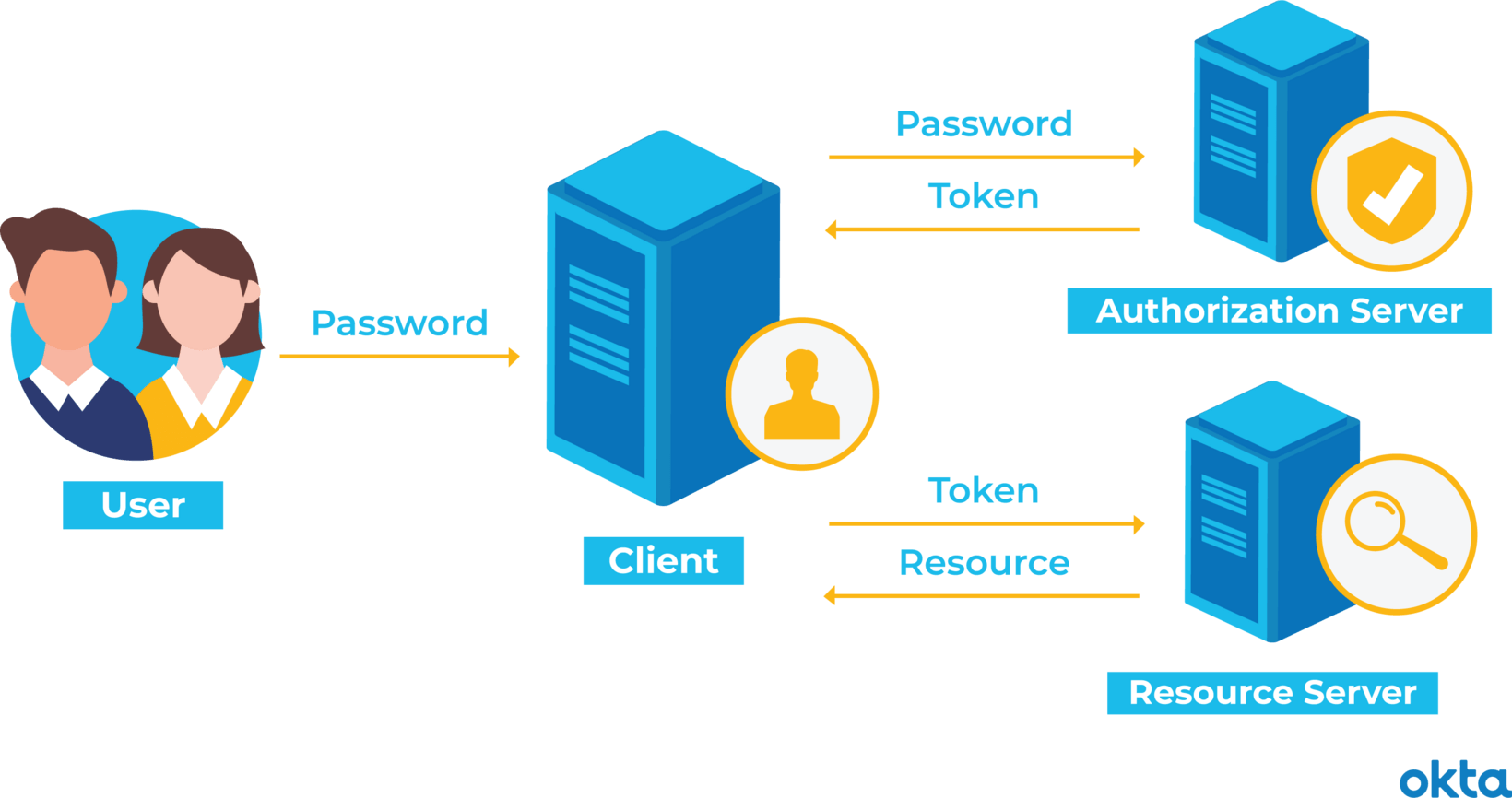
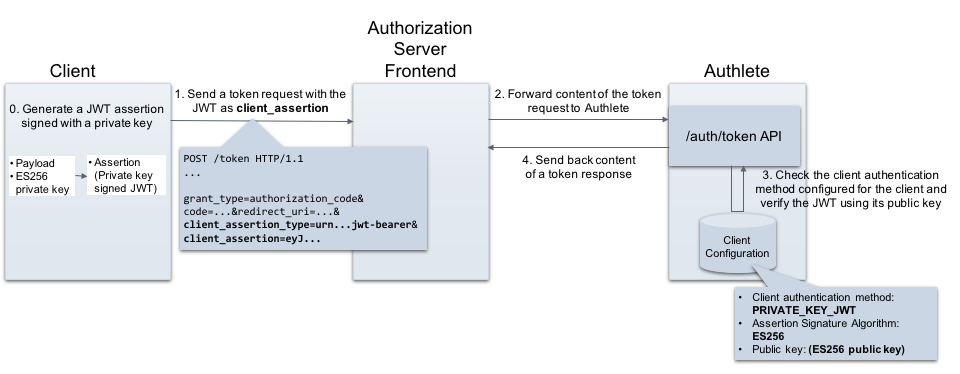
OAuth 2.0 Client Authentication. This article explains “OAuth 2.0 client… | by Takahiko Kawasaki | Medium



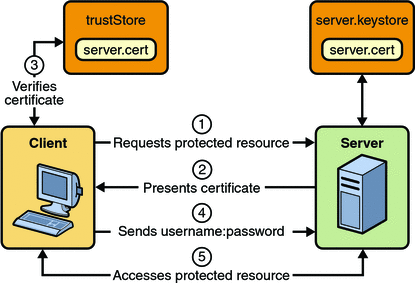


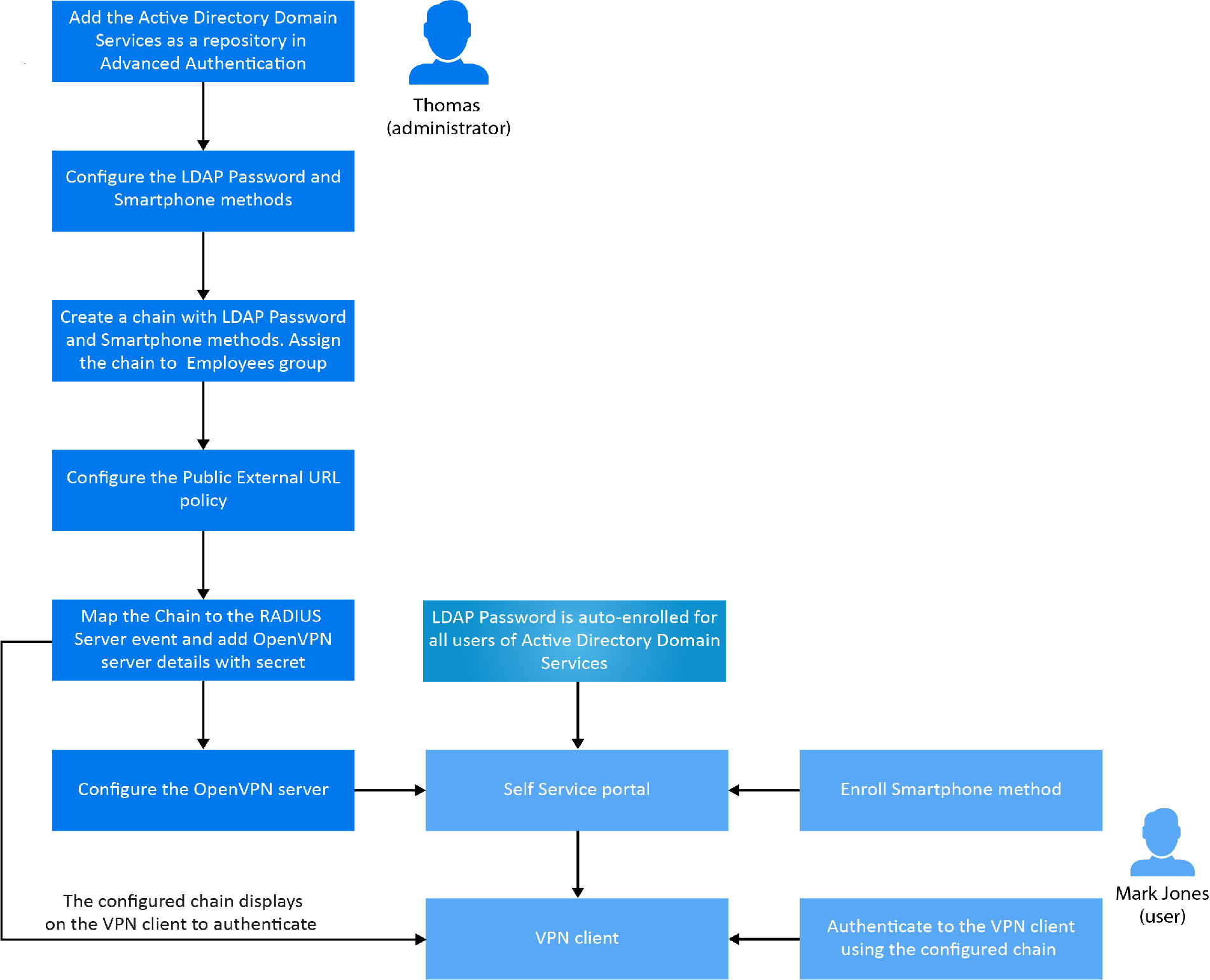

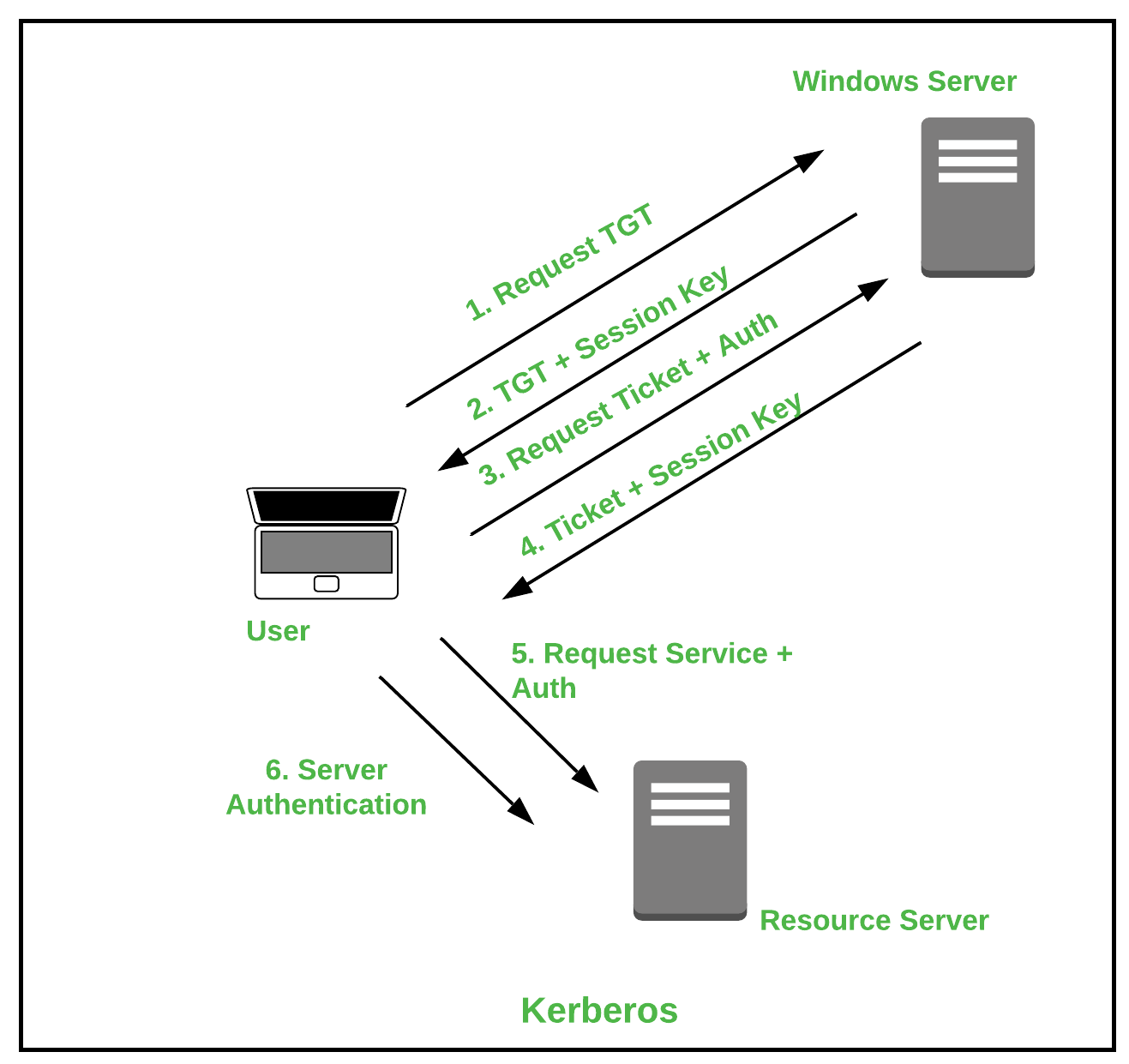
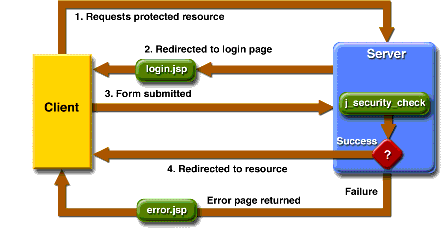
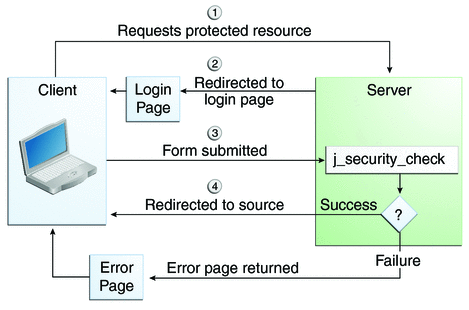

![RESOLVED] MySQL the server requested authentication method unknown to the client RESOLVED] MySQL the server requested authentication method unknown to the client](https://cdn-bhdil.nitrocdn.com/isrDVIFCpCXbHHPoNruCoFKRiVumSNxS/assets/static/optimized/rev-a6d8e2c/wp-content/uploads/MySQL_the_server_requested_authentication_method_unknown_to_the_client.png)